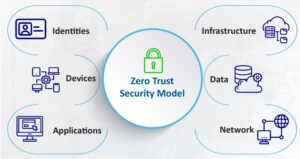
WHAT IS ZERO TRUST?
Trust is never constant nor absolute. It has always been a metric that alters with every network incursion, data leak, or ransomware attack. “Trust but verify” is its premise.
Recently, the rise in remote work increases the number of devices connecting to the network and the number of users connecting remotely. This leaves organizations with hundreds of thousands of potential vulnerabilities. A solution for this is Zero-Trust deployed by PKI (Public Key Infrastructure).
Zero Trust has been around as a concept for many years. Usually, when you sign into a website or your computer, trust is established right away. With mutual authentication, where the client must provide its certificate to the server, trust can be two-way when you access a secure site from a web browser over HTTPS with server certificate validation.
Passwords for users can be compromised, so by utilizing the “what you know” and “what you have” principle, two-factor authentication of the user becomes necessary.
Where does the idea of zero trust start from? This brings up the distinction between implicit and explicit trust as well as trust transfer (or transitive trust). Trust is a chain.
A vertical chain of trust is established starting with a root of trust at the local peer, and it crosses a horizontal chain of trust to go to the remote peer.
Trust must coexist throughout the lifecycle of linked things and start with trusted identities.
Thus, a zero-trust architecture is essentially a two-dimensional trust chain. Horizontally, The parties in a service transaction must show identification and zero compromise proof.
The assessment of verified integrity is trustworthiness. Verification of the entities’ identities is required vertically. A trust anchor is necessary for verifiable integrity because it acts as the foundation of trust for each actor in the chain.
PKI IS THE FOUNDATION FOR ZERO TRUST
Zero-Trust is primarily a security approach demanding constant validation to access a network. Zero users, devices, systems, or services are trusted— but anything connecting to the network must be verified.
So every time a user or device connects to the network it must be validated again.
In the Zero-Trust approach, instead of verifying digital identity based on IP addresses, digital identities are verified based on adaptive authentication methods such as PKI, multi-factor authentication (MFA), and single sign-on (SSO).
Its mantra is “Never trust, always verify”! Implementing Zero-Trust architecture hinges on a secure way to verify identity. PKI is a tried-and-true way to provide digital identity for a variety of use cases.
In fact, 96% of IT security executives believe that Public Key Infrastructure is essential to building a Zero-Trust architecture. This is because PKI provides the authentication, encryption, and integrity needed for the Zero-Trust model.
What PKI delivers:
- Authentication of identity of every user and device on the network.
- Encryption of all communications across the organization.
- Data & system integrity.
So, Zero Trust reduces security risk, complexity in the security stack, and the time taken to detect a breach. We at Acmetek deploy the Zero-Trust and are highly versed in simplifying identity and access management. Go Zero-Trust with us: https://www.acmetek.com/digicert-managed-pki-for-ssl/
ABOUT ACMETEK
Acmetek Global Solutions, Inc. is a privately held Digital Security Services Company serving USA & APAC clients in website security solutions since 2010.
The firm specializes in providing insight and expertise to enterprises, SMBs, governments, and provides a full range of Security Products, SSL, PKI, IoT, Malware Identity Scanning’s, Vulnerability Assessments, and Two-Factor Authentication.
Acmetek is a managed service partner of multi-brand technology solutions like CDW. We manage the Certificate Authority Practices of leading Website Security Brand, DigiCert (formerly known as Symantec).
Over a decade of experience in the security industry empowered us to grow as an Authorized Distributor/ Platinum Partner for DigiCert and a leading provider of security solutions and services.