


















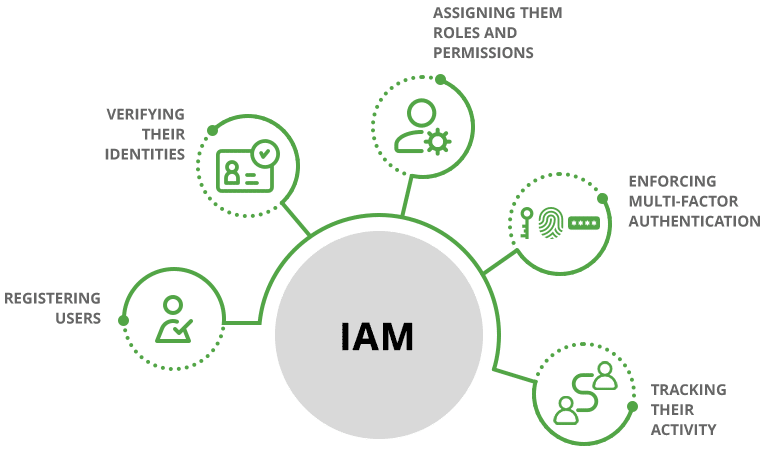
IAM is a cloud-based identity and access management (IAM) platform that helps organizations manage and secure the identities of their users, devices, and applications. It works by registering users, verifying their identities, assigning them roles and permissions, enforcing multi-factor authentication, and tracking their activity.

IAM likely provides SSO functionality, allowing users to log in once and access multiple applications and services without needing to re-enter credentials for each one.

IAM supports various MFA methods such as SMS codes, mobile apps, biometric authentication, and hardware tokens, enhancing security by requiring users to provide multiple verification forms before accessing resources.

IAM solutions allow administrators to define access policies and permissions based on user roles, responsibilities, and attributes, ensuring users have appropriate access to resources.

IAM offer tools for automated user onboarding (provisioning) and offboarding (de-provisioning) processes, helping streamline user lifecycle management.

Include features for managing user identities, access rights, and compliance through processes such as role-based access control (RBAC) and access certification.

Support federation protocols such as SAML and OAuth, enabling secure authentication and access across different domains and services. Single Logout allows users to log out of all connected services with one action.

Offer audit logs and reporting capabilities to track user activities, changes to access permissions, and other critical events for security and compliance purposes.

Setting-up your own IAM have numerous hidden risks and costs that are not immediately apparent. To avoid these issues, utilizing IAM is a highly effective strategy that can save you both time and money.

| DIV | IAM | |
|---|---|---|
|
Time Implementation
|
Slow
|
Faster implementation process.
|
|
Expertise
|
limited
|
Team of experts focused on you solutions 24/7.
|
|
Cost
|
Costs scale up
|
Cost-efficient with all Thales resources available.
|
|
Integration
|
limited
|
Integration with various applications, systems, and cloud services.
|
|
Scalability
|
Slow and costly
|
Solutions accommodate to organization's growth over time.
|

This report examines IDC’s study of global advanced authentication service providers and their surveyed customers. Learn about the authentication market and why IAM was recognized as a leading provider by downloading to this link.






As a trusted distributing partner of Identity Access Management (IAM), Acmetek is your gateway to unlocking the power of IAM for your organization. Here’s why Acmetek stands out:


"We have updated our PRIVACY POLICY and encourage you to read it by clicking here. Acmetek uses cookies, web beacons and log files to automatically gather, analyze, and store non-personal information about website visitors. This information is used to improve Acmetek’s services and your experience. To learn how to limit/opt-out these cookies within your browsers privacy control click here."
Accepted