Email is one of the most popular communication tools worldwide, used by individuals and businesses alike to share sensitive information, such as personal data, financial information, and business trade secrets. As a result, email security is essential to protect this information from falling into the wrong hands.
What is email security, and how is it important?
Email security protects email messages from unauthorized access, use, disclosure, disruption, modification, or destruction. This includes protecting email accounts from hacking and malware and preventing unauthorized individuals from reading or intercepting email messages.
Email is often used to share sensitive information. If this information falls into the wrong hands, it can be used for identity theft, fraud, and other malicious purposes. Additionally, email security is essential for businesses of all sizes, as data breaches can lead to financial losses, reputational damage, and regulatory compliance issues.
What is digital trust, and why is it essential even for emails?
Digital trust is individuals’ and businesses’ confidence in digital transactions and interactions’ security, privacy, and reliability. The term includes trust in the organizations that provide digital products and services, as well as trust in the technologies that are used to protect and share digital information.
Digital trust is vital for emails because it allows individuals and businesses to communicate confidently. When people know that their email accounts are secure and their messages will be protected, they are more likely to use email to share sensitive information. This can lead to greater productivity, improved collaboration, and increased innovation.
This blog will discuss the importance of email security and digital trust. We will also provide tips on how to build and sustain digital trust through secured email.
How Security Works in Emails: There Are a Lot More Behind Information Exchange
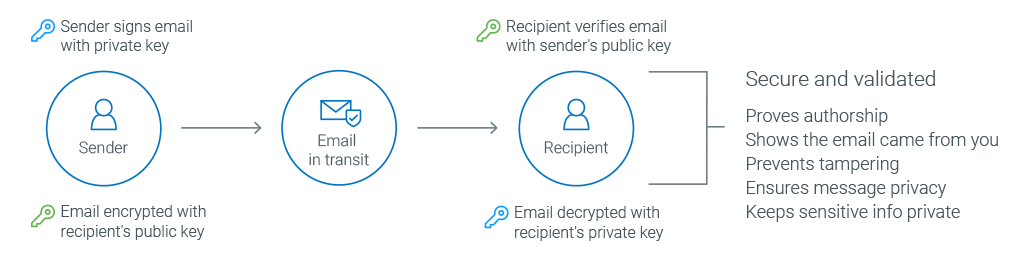
Email security uses various cryptographic techniques to encrypt email messages and protect them from unauthorized access, use, disclosure, disruption, modification, or destruction.
One of the most critical security measures in email is TLS encryption. TLS encrypts email messages as they travel the internet, preventing unauthorized individuals from intercepting and reading them.
Another important security measure is end-to-end encryption. End-to-end encryption encrypts email messages at the sender’s device and can only be decrypted by the intended recipient’s device. Even if an email server is compromised, the messages will remain secure.
SSL/TLS certificates create a secure connection between an email server and a web browser. These certificates ensure that email messages are encrypted in transit and cannot be intercepted by unauthorized individuals.
Email filtering can also be used to protect against spam and phishing emails. Spam emails are unwanted emails often used to spread malware or collect personal information. Phishing emails are fraudulent emails designed to trick users into revealing sensitive information, such as passwords or credit card numbers.
Email filtering uses various techniques to identify and block spam and phishing emails. These techniques include:
- Content filtering: Content filtering looks for keywords and phrases commonly used in spam and phishing emails.
- Heuristic filtering: Heuristic filtering uses machine learning to identify suspicious emails.
- Sender reputation filtering: Sender reputation filtering looks at the reputation of the sender of an email to determine if it is likely to be spam.
In addition to TLS encryption, end-to-end encryption, and email filtering, several other security measures can be used to protect email accounts.
MSPs can provide a variety of security services, including email security. MSPs can help you to implement and manage security solutions, and they can also monitor your email systems for threats.
IoT certificates can be used to secure the communication between IoT devices and email servers. These widely used certificates protect a wide array of IoT devices and gadgets from being compromised and used to steal personal data, even attack email servers.
IAM solutions can be used to control who has access to email accounts and other IT resources. IAM prevents unauthorized individuals from accessing sensitive information and organizes authorized access for a better user experience.
On the personal level, using strong passwords, enabling two-factor authentication, and keeping email software up to date are impactful actions that will help secure your email, even when using another device at another location.
Individuals and businesses can help protect their email accounts and build digital trust by taking these steps. A single protection method can go a long way in the digital highways.
Protecting and Respecting Privacy is a Measure of Trust
Privacy is essential for both individuals and businesses. Email providers should have clear and transparent data collection and usage policies, data encryption policies, and data retention policies, and give users control over their personal information.
Email providers should have clear and transparent data collection and usage policies. These policies should explain what type of data is collected, how it is used, and with whom it is shared. For example, an email provider may collect data on the following:
- The sender and recipient of an email
- The subject line of an email
- The date and time an email is sent and received
- The size of an email
- The IP address of the sender and recipient
- The type of device used to send and receive an email
Email providers may use this data to improve their services, such as by filtering spam and phishing emails, or to personalize the user experience, such as by recommending relevant content. Email providers may also share this data with third-party advertisers, but they should only do so with the user’s consent.
Email providers should encrypt all data at rest and in transit. This method helps to protect data from unauthorized access, even if an email server is compromised.
Email providers should have clear data retention policies. These policies should explain how long data is stored and when it is deleted. For example, an email provider may keep email messages for a certain period after the user deletes them, but they should eventually delete them permanently.
Email providers should give users control over their personal information. The freedom of power should include the ability to opt in or out of data sharing and to delete their accounts. For example, a user should be able to opt out of having their data shared with third-party advertisers, and they should be able to delete their email account and all of the associated data at any time.
Here is an example of how a data collection and usage policy might be written:
“Data collection and usage policy
We collect the following data when you create an account with us:
- Your name
- Your email address
- Your password
We use this data to create and manage your account and provide our services. We may also use this data to personalize the user experience and to send you marketing communications.
We will not share your data with third-party advertisers without your consent.
You can opt out of receiving marketing communications anytime by clicking the unsubscribe link in our emails. You can also delete your account and all associated data at any time by contacting us.”
By having clear and transparent privacy policies, email providers can help to build digital trust with their users. Users should understand what data is being collected, how it is being used, and with whom it is being shared. Users should also have control over their personal information, including the ability to opt in or out of data sharing and to delete their accounts.
Transparency and Accountability is a Must to Build Trust
Transparency is essential for building digital trust. Email providers should be transparent about their security policies and procedures, privacy policies and procedures, and incident response plans.
Security policies and procedures
Email providers should have clear and transparent security policies and procedures. These policies should explain how email accounts are protected and how data is handled. For example, an email provider may have policies on the following:
- Password security
- Two-factor authentication
- Data encryption
- Email Filtering
- Security incident response
Email providers should also publish their security policies on their website and make them available to all users.
Privacy policies and procedures
Email providers should have clear and transparent privacy policies and procedures. These policies should explain what type of data is collected, how it is used, and with whom it is shared. For example, an email provider may collect the following data:
- The sender and recipient of an email
- The subject line of an email
- The date and time an email is sent and received
- The size of an email
- The IP address of the sender and recipient
- The type of device used to send and receive an email
Email providers may use this data to improve their services, such as by filtering spam and phishing emails, or to personalize the user experience, such as by recommending relevant content. Email providers may also share this data with third-party advertisers, but they should only do so with the user’s consent.
Email providers should also publish their privacy policies on their website and make them available to all users.
Incident response plans
Email providers should have incident response plans in place to deal with security breaches. These plans should explain how email users will be protected and compensated for the event. For example, an email provider may have a plan to notify users of a breach, assist them in changing their passwords, and compensate them for any financial losses they incur due to the violation.
Email providers should also publish their incident response plans on their website and make them available to all users.
Accountability
Accountability is vital for building digital trust. Email providers should be accountable for their security and privacy practices. The burden of provision should be given to more than just the users but mainly to the provider, who is expected to have these resources available.
Email providers should have independent security audits performed on their systems and procedures. This method helps ensure that the provider meets its security commitments and that their strategies are objectively effective.
Email providers should have data breach insurance in place. This helps to protect users in the event of a data breach.
Email providers should commit to customer service. Services include providing users with timely and helpful support when they have questions or problems.
By being transparent and accountable, email providers can help to build digital trust with their users. Users should be able to understand how their email accounts are protected and how their data is handled. Users should also be able to rely on their email provider to protect them in case of a data breach.
Example
Here is an example of how a security policy might be written:
“We are committed to protecting your email account’s and data’s security. We have implemented several security measures to protect your account, including:
- Password encryption
- Two-factor authentication
- Data encryption
- Email Filtering
- Security incident response
We also have a team of security experts constantly monitoring our systems for threats.
In the event of a security breach, we will notify you immediately and take steps to mitigate the damage. We will also compensate you for any financial losses you incur due to the violation.
If you have any questions or concerns about our security policy, please do not hesitate to contact us.”
Conclusion
Building and sustaining digital trust through secured email is essential for individuals and businesses. By protecting your email account, you can help protect yourself from various threats and build trust with others.
Email providers should also build digital trust by being transparent and accountable for their security and privacy practices. Email providers should have clear and transparent security policies and procedures, privacy policies and procedures, and incident response plans. Email providers should also be subject to independent security audits and have data breach insurance in place.
To learn more about securing your email account and building digital trust, please visit Acmetek.com. You can also subscribe to our newsletter for the latest news and tips on email security. Don’t hesitate to get in touch with our support team if you have any questions or would like to schedule a demo of our digital security solutions.